How Managed Data Protection Helps Ensure Business Continuity and Recovery
How Managed Data Protection Helps Ensure Business Continuity and Recovery
Blog Article
Just How Managed Information Security Safeguards Your Service From Cyber Hazards
In an era where cyber hazards are significantly advanced, the significance of managed information security can not be overstated. Organizations that carry out detailed protection measures-- such as information encryption, accessibility controls, and continuous tracking-- are much better equipped to safeguard their delicate details.
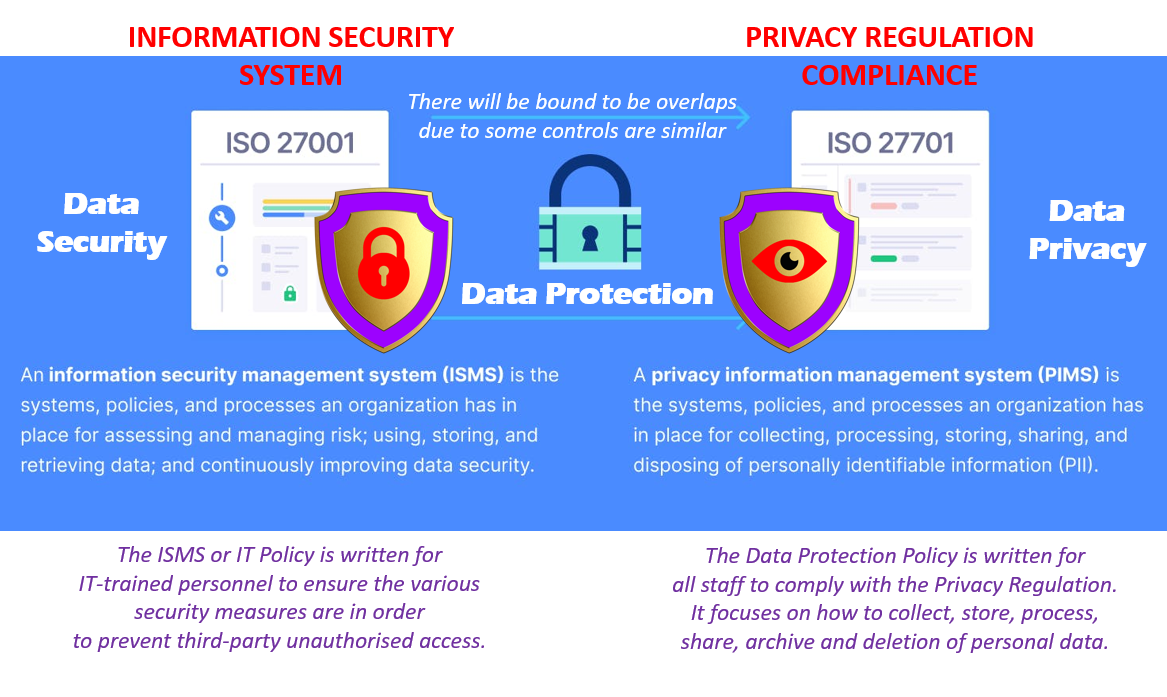
Recognizing Managed Information Protection
Managed information security is an important part of modern cybersecurity strategies, with around 60% of companies choosing such services to protect their crucial info assets. This approach includes contracting out data security duties to specific provider, permitting organizations to concentrate on their core service functions while making sure durable protection procedures are in place.
The essence of handled information protection hinges on its capacity to provide comprehensive remedies that include information backup, recuperation, and danger detection. By leveraging innovative technologies and know-how, took care of service companies (MSPs) can implement positive procedures that minimize risks connected with information breaches, ransomware strikes, and other cyber threats. Such solutions are designed to be scalable, suiting the advancing demands of businesses as they adapt and grow to new challenges.
In addition, took care of data security assists in compliance with regulatory requirements, as MSPs typically remain abreast of the current sector standards and techniques (Managed Data Protection). This not just boosts the security position of a company however additionally imparts self-confidence amongst stakeholders concerning the integrity and privacy of their information. Ultimately, understanding managed information protection is crucial for organizations looking for to strengthen their defenses versus the ever-changing landscape of cyber threats
Secret Components of Data Defense
Efficient data security techniques normally encompass several vital parts that operate in tandem to guard delicate information. Primarily, data file encryption is crucial; it changes understandable data right into an unreadable style, making certain that also if unauthorized accessibility occurs, the information stays secured.
Access control is another essential element, allowing companies to limit information accessibility to authorized personnel just. This decreases the threat of interior breaches and improves liability. Routine information backups are necessary to ensure that details can be brought back in the occasion of data loss or corruption, whether due to cyberattacks or accidental deletion.
Next, a robust protection plan must be developed to lay out procedures for data dealing with, storage, and sharing. This plan must be regularly upgraded to adapt to evolving hazards. Additionally, continuous tracking and auditing of information systems can find abnormalities and potential violations in real-time, facilitating speedy actions to threats.
Benefits of Managed Provider
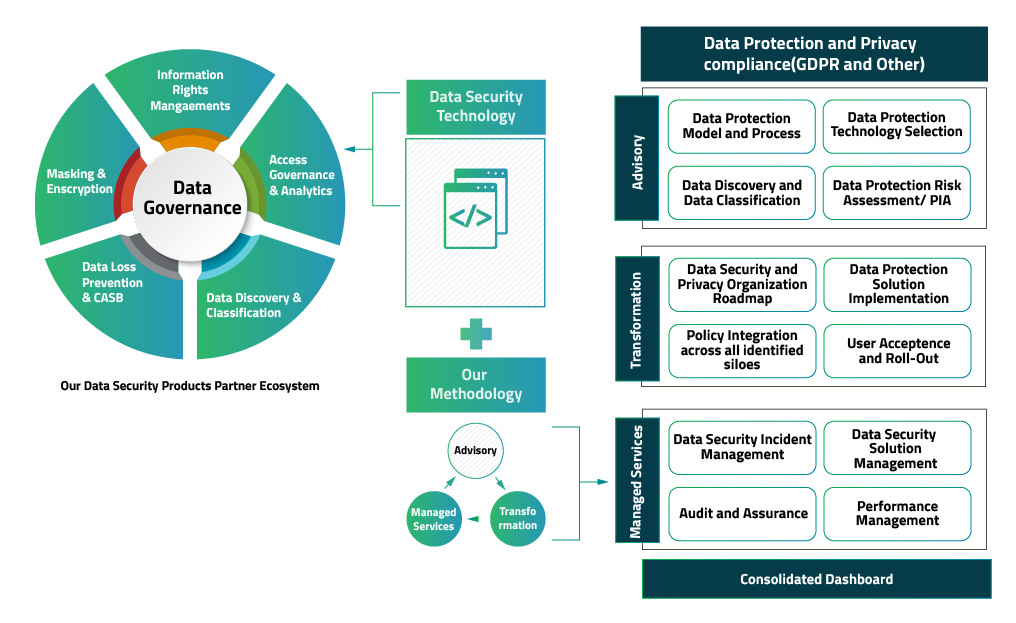
In addition, took care of services help with positive surveillance and threat detection. MSPs make use of sophisticated modern technologies and tools to constantly keep track of systems, guaranteeing that anomalies are recognized and attended to prior to they intensify right into major concerns. This positive strategy not only minimizes action times but additionally alleviates the potential impact of cyber events.
Cost-effectiveness is one more key advantage. By contracting out data security to an MSP, companies can avoid the considerable costs related to internal staffing, training, and technology investments. This enables business to allocate sources extra efficiently while still taking advantage of top-tier protection options.
Conformity and Regulative Assurance
Making certain conformity with sector laws and requirements is an essential element of data security that organizations can not overlook. Governing structures, such as GDPR, HIPAA, and PCI DSS, enforce rigorous requirements on exactly how services handle and safeguard sensitive information. Non-compliance can lead to severe fines, reputational damage, and loss of consumer trust.
Managed information defense solutions assist organizations browse the complicated landscape of conformity by executing durable safety and security steps tailored to satisfy details regulatory demands. These solutions provide systematic strategies page to information security, gain access to controls, and regular audits, ensuring that all protocols align with legal responsibilities. By leveraging these handled solutions, organizations can preserve constant oversight of their data defense approaches, making certain that they adjust to developing laws.
Additionally, thorough reporting and paperwork offered by handled information protection solutions function as valuable devices throughout conformity audits. These documents demonstrate adherence to established procedures and criteria, supplying guarantee to stakeholders and regulative bodies. Ultimately, purchasing handled data defense not only strengthens an organization's cybersecurity pose yet additionally infuses self-confidence that it is committed to maintaining compliance and regulative assurance in a significantly complicated digital landscape.
Selecting the Right Provider
Picking the ideal handled data defense service provider is important for companies intending to boost their cybersecurity frameworks. The very first step in this process is to review the carrier's knowledge and experience in the area of information defense. Look for a company with a proven record of successfully protecting organizations versus various cyber dangers, in addition to knowledge with industry-specific regulations and conformity demands.
Furthermore, examine the variety of services supplied. A comprehensive service provider will provide not only backup and recovery solutions yet additionally positive hazard detection, danger analysis, and event action capacities. It is crucial to ensure that the carrier employs innovative modern technologies, consisting of encryption and multi-factor verification, to safeguard delicate data.
A receptive assistance group can considerably affect your organization's capacity to recover from cases promptly. By very carefully evaluating these variables, organizations can make a notified decision and pick a company that aligns with their cybersecurity goals, inevitably strengthening their defense versus cyber risks.
Final Thought
To conclude, took care of information protection acts as an important defense against cyber hazards by utilizing robust safety and security procedures, specific proficiency, and progressed modern technologies. The assimilation of extensive strategies such as information security, access controls, and have a peek here continual surveillance not only mitigates dangers but likewise ensures compliance with regulative standards. By contracting out these services, organizations can enhance their safety structures, promoting quick healing from data loss and fostering self-confidence amongst stakeholders despite ever-evolving cyber dangers.
In a period where cyber hazards are significantly advanced, the relevance of managed data protection can not be overemphasized.The essence of handled information defense lies in its ability to supply thorough services that include information backup, recovery, and hazard discovery. Eventually, recognizing taken care of information defense is essential for useful content organizations looking for to fortify their defenses against the ever-changing landscape of cyber dangers.

In final thought, took care of data protection serves as an essential protection versus cyber hazards by employing durable safety procedures, specific know-how, and advanced innovations. Managed Data Protection.
Report this page